Preface
There are many companies with different brands of AI based antivirus (AV), each using variations of machine learning and deep learning to achieve the goal of an autonomous AV protection. This report will take a holistic view of the emerging technology as opposed to the specifics of each variation on the technology as the end goal of all these products is the same; automated AV protection.
What is Artificial Intelligence based Antivirus and why do we need it?
It’s an unfortunate fact that the internet is not a safe place. Cyber criminals are a real and ever present threat in today’s society. There were 3.8 billion internet users in 2017 and this is expected to grow to 6 billion by 2022 (Cyber Security Ventures, 2017, pg 4). The majority of internet users understand they need an up to date antivirus to protect themselves from malicious software. The issue is traditional antivirus software has its limitations and the scale of the task has quickly outgrown the capability of humans to manage (Microsoft’s Global Incident Response and Recovery Team, cited in Cyber Security Ventures, 2017, pg 8).
According to the Australian Cyber Security Centre (2017), cyber crime will continue to be an attractive option for criminals due to its low risk and high reward. In 2017 the average time globally to detect an intruder on a network was 101 days (FireEye, 2017) and Cyber Security Ventures (2017) estimates that cyber crime will cost over 6 trillion annually by 2021. Traditional anti-virus software is reactive in nature and is unable to protect your system from a zero day exploit as it requires a human operator to classify the threat and update the data base. Cyber Security Ventures (2017) predicts that by 2021 newly reported zero day exploits could be as high as one per day.
A possible solution to these limitations being developed now is the use of Artificial Intelligence or Machine Learning in AV technology. This technology is capable of autonomously identifying and preventing cyber threats. AI utilises its superior pattern recognition to identify malware (Rosner 2017); this includes zero day exploits.
Armstrong (2017) describes Artificial Intelligence is any technology that mimics human behavior and is programmed to react like humans do. AI can collect data and make its own decisions based on that information without human input. Armstrong (2017) also describes Machine learning as a form of AI that can learn something without it being specifically programmed with that information by an operator.
How is Artificial Intelligence Antivirus created and how does it work?
The most recent form of AI being utilised in AV is deep learning. Deep Instinct (2018) identifies eight steps in the creation of an AI based anti-malware solution utilising deep learning.
- Preparation – Millions of data samples are prepared by data scientists; this includes clean and malicious code.
- Training – The ‘Brain’ is exposed to this raw data in a continuous loop and learns to instinctively identify malicious code.
- Detection – The ‘Brain’ can instinctively detect malicious software.
- Prediction – The ‘Brain can now predict whether a file is malicious or not.
- Agent Creation – The ‘Brain’ is compressed into an ‘Agent’. This retains all of the abilities of the ‘Brain’ in a much smaller file size.
- Agent Insertion – The ‘Agent’ is inserted onto the system that requires protection.
- Protection – The ‘Agent’ checks every file before it executes for malicious code.
- Prevention – The ‘Agent’ knows how to identify malicious software and is capable of identifying ‘zero day’ exploits.
Traditional Antivirus software scans a file and compares specific bits of code against its database. This database is maintained and updated by analysts who, once malicious code has been identified, upload the signature to the database for future identification (Comodo 2018).
A brief history of Artificial Intelligence
The study of Deep learning originated from a desire to produce a computer system that can simulate the human brain. (Wang, Raj & Xing 2017).
1940s – Early machine learning was heavily based on the current theories of how the brain works. Walter Pitts and Warren McCulloch had developed
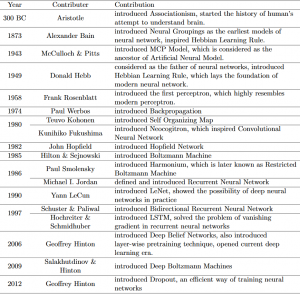
techniques that mimicked the way a neuron was thought to have worked. This was known as ‘threshold logic unit’ (Beam 2017), which mimicked a thought process through the use of a combination of algorithms and mathematics (Foote 2017).
1947 to 1980 – The first AI winter; this period saw reduced funding for AI research. Two limitations had developed at the time, these were insufficient memory and processing speeds. AI research resumed in 1980 as the US and British governments wanted to compete with Japan’s computer development (Foote 2016).
1979 – The first conventional neural network was developed by Kunihiko Fukushima; called ;Neocognitron’ which was capable of learning to identify and recognise visual patterns (Foote 2017; Wang, Raj & Xing 2017, p.35).
1989 – Yann LeCun conducted a practical demonstration of a neural network with back propagation, using errors in training of deep learning models. This system was able to read handwritten digits. This was eventually used to read numbers on handwritten checks (Beam 2017; Foote 2017).
1985 to 1990s – The second AI winter; this resulted from an overstated ability of AI at the time and the disappointment when these expectations were not met. This resulted in a second perios of reduced funding for development (Foote 2017).
1999 – A significant step for deep learning as computers became more powerful. Faster data processing and the development of GPUs (graphical processing units) for processing images (Foote 2017).
2005 – Defense Advanced Research Projects Agency (DARPA) set a 2 million (USD) prize for anyone who can build a vehicle that could self navigate the Nevada Desert, USA (DEFCON24 2016).
2006 – The term ‘Deep Learning’ as coined and replaced ‘neural network’ due to a new method of machine learning being utilised. This system involved training a few layers then adding additional layers as each layer is trained; hence the term ‘Deep Learning’ (Beam 2017).
2012 – A small breakthrough using deep nets for speech recognition (Beam 2017). The focus of this is to create natural sounding speech. This is the basis for talking assistant technology like Apple’s Siri (Apple 2018; Foote 2016).
2016 – DARPA again posted a challenge with a 2 million (USD) reward, for anyone who can develop a computer that can autonomously hack and patch unknown software (DEFCON24 2016).
2017 – Cylance released first consumer AI powered antivirus product: CylancePROTECT® Home edition. Currently the home based product is only available to employees of companies that utilise Corporate Cylance products (Cylance 2017).

Impact AI based Antivirus technology
Cyber security professional shortage – It is estimated that by 2020 there will be a shortage of more than 1.5million security professionals and as the internet of things (IOT) continues to grow; the size of the job protecting it all also grows (Dellinger 2017). Some of this shortage and scale could be offset by the proliferation of AI based antivirus technology. Less security professionals would be required to monitor more systems through AI automation.
Increase in cyber threat capability – Although this is an emerging technology, it has the potential to be disruptive to a small degree. It is possible in the future once AI based antivirus has become the norm; that cyber criminals will be forced to adapt to this change and may look to utilise AI technology to conduct their attacks. The use of AI could expand their current abilities and enable the development of new threats, possibly initiating an AI arms race (Brundage et al, 2018, pg 5). This will become a necessary step as AI based antivirus is capable pf preventing 99% of malware before it can execute on the system. This includes spear phishing, malicious programs and even zero day malware (Cylance 2018). According to Brundage et al, (2018, pg 17) the current openness of AI research and ease of obtaining source code, could provide cyber criminals this enhanced capability. It sounds like science fiction but its not unreasonable to think in the future AI hackers will be utilised to breach AI protected systems. In 2016 DEF CON hosted the world’s first all machine hacking tournament, the Cyber Grand Challenge (DEFCON24 2016).
Business shift – The improvements over conventional antivirus software will likely see a shift towards this technology due to its effectiveness and ability to prevent malicious attack without human guidance. Conventional antivirus providers will need to upgrade to an AI based solution or risk being being left behind. A research summary conducted by Doug and Poller (2017) indicates that of all respondents 47% have already deployed a machine learning based technology as part of their cyber security program with an additional 23% currently engaged in trials. This means over 50% of respondents have already begun integrating an AI solution into their cyber defense. Interestingly on 3% of respondents did not see the value in AI based antivirus technology, which may indicate a lack of trust in new technology or an unwillingness to change.
Conclusion
This was a brief look at the emergence of Artificial Intelligence in Antivirus technology. After conducting the research and seeing the benefits over traditional AV systems, I believe this is the natural evolution. Cyber criminals are able to develop new threats every day so the world needs a system that can intuitively identify a threat before it strikes.
Bibliography
Apple 2018, Siri, Apple Inc, retrieved 20 Apr 2018, <https://www.apple.com/au/ios/siri/>.
Armstrong, P 2017, Disruptive Technologies : Understand, Evaluate, Respond, Kogan Page, London, UNITED KINGDOM.
Australian Cyber Security Centre 2017, ACSC 2017 Threat Report, retrieved 18 April 2018, <https://www.acsc.gov.au/publications/ACSC_Threat_Report_2017.pdf>.
Beam, AL 2017, Deep Learning 101 – Part 1: History and Background, 20 Apr 18, 23 Feb 2017, <https://beamandrew.github.io/deeplearning/2017/02/23/deep_learning_101_part1.html>.
Brundage, M, Avin, S, Clark, J, Toner, H, Eckersley, P, Garfinkel, B, Dafoe, A, Scharre, P, Zeitzoff, T, Filar, B, Anderson, H, Roff, h, Allen, GC, Steinhardt, J, Flynn, C, hEigeartaigh, SO, Beard, S, Belfield, H, Farquhar, S, Lyle, C, Crootof, R, Evans, O, Page, M, Bryson, J, Yampolskiy, r & Amodei, D 2018, The Malicious Use of Artificial Intelligence: Forecasting, Prevention, and Mitigation, Future of Humanity Institute.
Comodo 2018, How Antivirus Works, Comodo Security Solutions, retrieved 20 Apr 2018, <https://antivirus.comodo.com/how-antivirus-software-works.php>.
Cyber Security Ventures 2018, 2017 Cyber Crime Report, retrieved 18 April 2018, <https://cybersecurityventures.com/2015-wp/wp-content/uploads/2017/10/2017-Cybercrime-Report.pdf>.
Cylance 2017, Cylance Revolutionizes Consumer Security Market with First AI Driven Next-Generation Antivirus – CylancePROTECT Home Edition, Cylance Inc, 03 Aug 2017, <https://www.cylance.com/en_us/about/news—press/cylance-revolutionizes-consumer-security-market-with-first-ai-driven-next-generation-antivirus-cylanceprotect-home-edition.html>.
Cylance 2018, CylancePROTECT, Cylance Inc, retrieved 22 Apr 2018, <https://www.cylance.com/en_us/products/our-products/protect.html>.
DeepInstinct 2018, What is Deep Learning, Deep Instinct, retrieved 20 Apr 2018, <https://www.deepinstinct.com/how-it-works/>.
DEFCON24 2016, DEF CON 24 Cyber Grand Challenge, retrieved 22 Apr 2018, <https://www.defcon.org/html/defcon-24/dc-24-cgc.html>.
Dellinger, A 2017, ‘Will Artificial Intelligence Solve Cybersecurity—And Put Experts Out Of Work?’, International Business Times, retrieved 21 Apr 2018, <http://www.ibtimes.com/will-artificial-intelligence-solve-cybersecurity-put-experts-out-work-2595731>.
Doug, C & Poller, J 2017, Top of mind Threats and Their Impact on Endpoint Security Decisions, research summary, Enterprise Security Group, retrieved 22 Apr 2018, https://www.cylance.com/content/dam/cylance/pdfs/reports/ESG-Research-Insights-Report-Summary-Cylance-Oct-2017.pdf.
FireEye 2018, M-Trends 2018, FireEye, retrieved 18 April 2018, <https://www.fireeye.com/content/dam/collateral/en/mtrends-2018.pdf>.
Foote, KD 2016, ‘A Brief History of Artificial Intelligence’, retrieved 20 Apr 2018, <http://www.dataversity.net/brief-history-artificial-intelligence/>.
Foote, KD 2017, ‘A Brief History of Deep Learning’, retrieved 20 Apr 2018, <http://www.dataversity.net/brief-history-deep-learning/>.
Rosner, M. 2017, ‘Why Artificial Intelligence is the Future for Endpoint Security’, Updates from the front lines of the AI & IoT revolution, weblog post, 01 Nov 2017, retrieved 22 Apr 2017, https://www.sparkcognition.com/2017/11/artificial-intelligence-future-endpoint-security-2/
Wang, H, Raj, B & Xing, EP 2017, ‘On the origin of deep learning’, arXiv preprint arXiv:1702.07800.
